A few weeks ago, our Mobile Developer Emanuele Maso spoke about passkeys at DevFest Vicenza, an event hosted by the Google Developer Group Vicenza – a fresh and energizing community of tech and software development enthusiasts ready to learn something new, keep up to date with the latest news, and network with like-minded people.
Emanuele’s speech focused on the importance of Passkeys authentication and demonstrated it in action with a demo app built for iOS and Android with Compose and Kotlin Multiplatform.

What are Passkeys?
Passkeys are a safer and easier alternative to passwords designed by the FIDO Alliance. With Passkeys, users can sign in to apps and websites using a biometric sensor, such as a fingerprint or facial recognition, PIN, or pattern.
A Passkey is a digital credential, tied to a user account and a website or application, which allows users to authenticate without friction or any additional authentication factor. This technology aims thus to replace legacy authentication mechanisms like passwords.
Authentication with Passkeys
If an app or website supports passkey authentication, you will find a button to register a Passkey on your account or sign up using a Passkey.
The user enters their username/email, initiating the enrollment process. If the user’s device approves, it prompts the credential manager to securely save the newly created credentials.
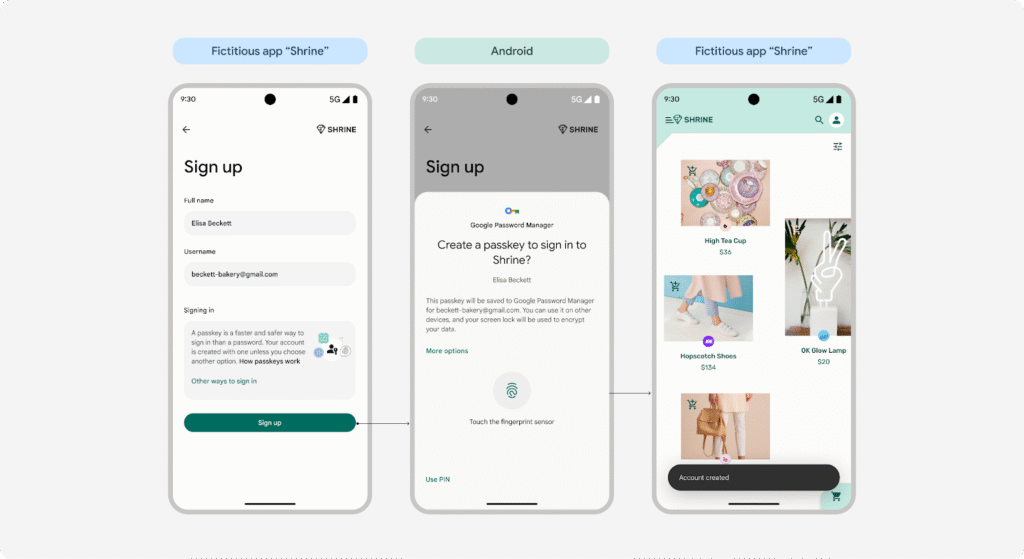
Once the new credential has been successfully registered, the user will be able to sign in by authenticating through the credential manager where the passkeys are stored.
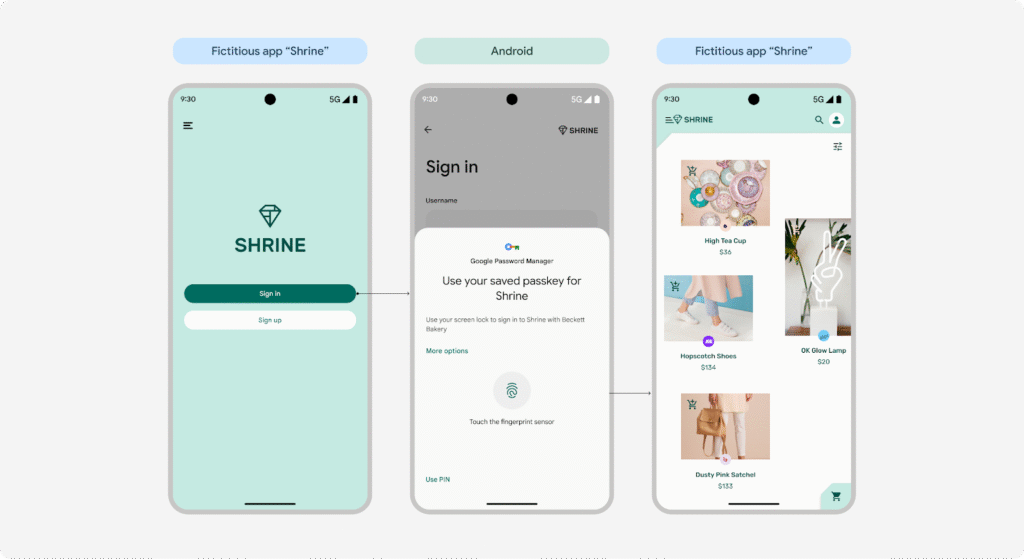
Advantages and limitations
Authentication with Passkeys offers numerous advantages:
- More secure than passwords by design, protecting users from exposing sensitive information.
- Phishing attack resistant: a fake website cannot scam users by impersonating the real one. The system verifies the website’s authenticity and prompts passkey selection only for legitimate websites with stored passkeys in the credential manager.
- Platform breach resistant: the private key is never exposed; the platform only stores a public key.
- Easier than ever: no need to create and remember passwords; users authenticate with their device, and the system handles the rest.
- Cross-device option available: users can authenticate on a website using a Passkey created on their mobile device.
What about mobile apps? Users can already authenticate with Passkeys with the apps that support this method. There are just few limitations based on their device:
iOS
- Allowed for device-bound passkeys from iOS 15+
- iCloud Keychain for cloud syncing passkeys from iOS 16+
- Support for Third Party Passkeys Managers from iOS 17+
Android
- Passkeys available from Android 9+
- Support for Third Party Passkeys Managers available from Android 14+
A Mobile Developer’s Perspective

From a mobile app developer’s perspective, integrating Passkeys requires working with the operating system’s credential management APIs. Although the FIDO Alliance standardizes the underlying protocols (WebAuthn), each platform offers unique SDKs and frameworks to expose this functionality to app developers. This approach simplifies the process by handling the cryptographic complexities, letting developers prioritize user experience.
The Passkeys authentication is based on a series of complex but secure interactions between the user’s device, the application, and the service’s server. Initially, during registration, the user starts the process, and the server generates a “cryptographic challenge,” a unique and random piece of data that the device must digitally sign. This challenge and other information are sent to the user’s device via the app. The device, through its credential manager such as iCloud Keychain or Google Password Manager, creates a key pair: a private key, kept secret, and a public key. The challenge is signed with the private key, and the public key, along with the signature, is sent to the server, which stores it associated with the user’s account.
Subsequently, during authentication, the user attempts to log in and selects the Passkey option. The server generates a new challenge, sends it to the device, which signs it with the previously created private key. The signature is then sent to the server, which verifies it using the stored public key. If the signature is valid, the user is authenticated.
Some fundamental concepts are the “challenge,” a string of random data for each request, the cryptographic “key pair,” where the private key signs and the public key verifies, and the “digital signature,” the result of signing the challenge with the private key.
Back-end configuration for Android and iOS
To properly implement Passkeys authentication on Android and iOS, configuring the back-end is crucial. This setup includes using `.well-known` files and other specific settings.
`apple-app-site-association` file for iOS
On iOS, an `apple-app-site-association` (AASA) file is required to link the iOS app to the website’s domain. This file tells the operating system that the app is authorized to handle certain domains. The AASA file must be hosted in the `/.well-known/` directory of the domain (e.g., https://your-app.com/.well-known/apple-app-site-association)
Structure of the `apple-app-site-association` file
{
"webcredentials": {
"apps": [
"ABCDE12345.com.example.app"
],
}
}
`
`assetlinks.json` file for Android
On Android, an `assetlinks.json` file is required to associate the Android app with the website’s domain. This file verifies that the app has the authority to manage credentials for the specified domain.
The `assetlinks.json` file must be hosted in the `/.well-known/` directory of the website domain (e.g., https://your-app.com/.well-known/assetlinks.json).
Structure of the `assetlinks.json` file
[
{
"relation": [
"delegate_permission/common.handle_all_urls",
"delegate_permission/common.get_login_creds"
],
"target": {
"namespace": "android_app",
"package_name": "com.your.app",
"sha256_cert_fingerprints": ["XX:XX:XX:XX:...:XX"]
}
}
]
Conclusions
It’s clear that Passkeys are the way to go for the future of authentication for websites and apps. Many companies are already supporting and pushing this method: Google, Apple, WhatsApp, and GitHub, just to name a few.
At Bitrock we are ready to face the new challenges ahead on this topic. If you want to learn more about Passkey authentication and discover our Mobile App Development solutions, visit our dedicated page.
Main Author: Emanuele Maso, Mobile Developer at @ Bitrock.

