Secure your access in a dynamic world
The current IT landscape is characterized by multiple challenges and quite a bit of them are related to the increasing dynamicity of the environments IT professionals are working in. One of these challenges is securing access to private services. The dynamic nature of the access manifests itself on multiple levels:
- Services: they tend to be deployed in multiple instances per environment
- Environments: hosts, where the workload is deployed, can change in a transparent way to the final user
- Users: people change role, people come and go from a team
- Credentials: the more often they are changed, the more secure they are
Tools developed when this kind of dynamism was not foreseeable are starting to show their limitations. For example, accessing a service would often mean to provide networking access to a subnet where careful network and firewall policies need to be set up. The resulting access is allowed to a user independently from their current role.
Zero trust in a dynamic environment
A Zero trust approach is highly desirable in every environment. Being able to assume zero trust and granularly providing access to resources with role based rules without the need to configure delicate resources like network and firewalls are paramount in a modern IT architecture.
This is even more so in a dynamic environment, where the rate of change can put under pressure the security teams and their toolchains as they try to keep access configurations up to date.
Boundary to the rescue
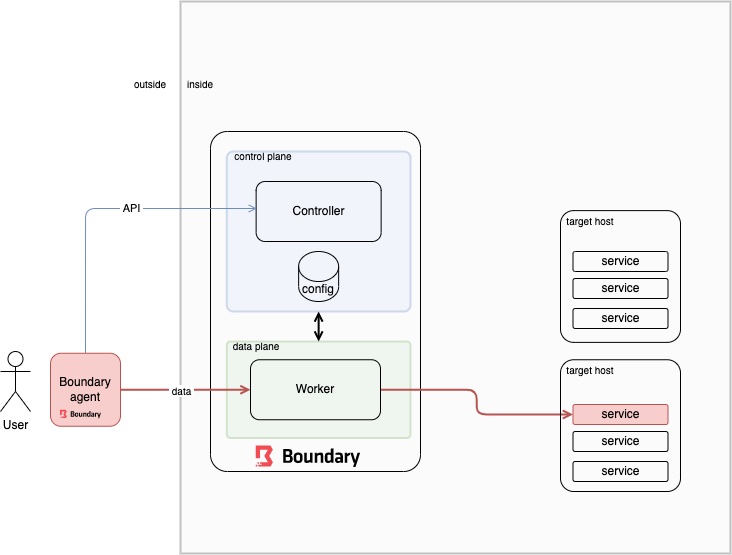
In the following diagram we can see how HashiCorp’s Boundary is designed to fulfill the requirements of granting secure access in a zero trust environment. The access to a remote resource is granted by defining policies on high level constructs that encapsulate the dynamic nature of the access.
The main components are:
- Controller (control plane): the admin user interacts with the controller to configure access to resources. The normal user interacts to ask for authentication / authorization.
- Worker (data plane): the connection is established between the local agent and the remote host by passing through this gateway that allows for the connection based on what the controller allows.
- Local Agent: interact with the controller and the worker to establish the connection.
Boundary concepts
Identity is a core concept in Boundary. Identity is represented by two types of resources, mapping to common security principals:
- Users, which represent distinct entities that can be tied to authentication accounts
- Groups, which are collections of Users that allow easier access management
Roles map users and groups to a set of grants, which provide the ability to perform actions within the system.
Boundary’s permissions model is based on RBAC and each grant string is a mapping that describes a resource or set of resources and the permissions that should be granted to them.
A scope is a permission boundary modeled as a container. There are three types of scopes in Boundary:
- a single global scope: which is the outermost container
- organizations: which are contained by the global scope
- projects: which are contained by orgs
Each scope is itself a resource.
Boundary administrators define host catalogs that contain information about hosts. These hosts are then collected into host sets which represent sets of equivalent hosts. Finally, targets tie together host sets with connection information.
Boundary interfaces
Boundary offers multiple interfaces to interact with the tool:
- a CLI that we DevOps engineers love
- a user friendly Desktop application
- a Web UI for the server
Integration is key
So how can this be kept up to date with the current dynamic environments?
The answer lies in the integrations that are available to add flexibility to the tool: specifically when it comes to the authentication of users, the integration with an identity provider with standard OIDC protocol can be leveraged. When it comes to credentials, the integration with HashiCorp Vault surely (pun intended) covers the need of correctly managed secrets with their lifecycle (Vault Credentials Brokering). Finally, when we talk about the list of hosts and services we can leverage the so-called Dynamic Hosts Catalog. The catalog can be kept up to date in a push mode by using the integration with HashiCorp Terraform or in a pull mode by interacting with HashiCorp Consul.
Want to get your feet wet?
Seems like this tool is providing a lot of value: so why not integrate it into your environment? We are already planning to add it into our open source Caravan tool.
There’s a high chance for you to get your feet wet playing with Boundary and other cool technologies, don’t be shy, join us on (the) Caravan.
Discover more on Zero Trust in our upcoming Webinar in collaboration with HashiCorp.
When: Thursday, 31st March 2022
Where: Virtual Event
More details available soon – Follow us on our Social Media channels to find out more!